Most IT pain isn’t outages—it’s daily friction. Audit the drag, fix quick wins, then decide if cloud truly simplifies your next chapter…
By Industry
Password resets are a tax. Passkeys are how we stop paying it.
Password resets are a tax. Passkeys can cut the bill—but only if they’re practical. Edge passkey sync removes a key objection, with a catch…
Busywork to Breakthrough: What to Automate First
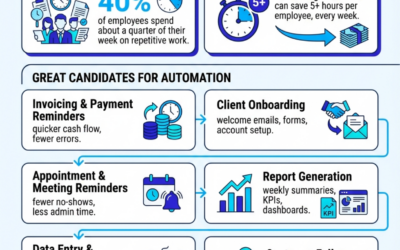
Busywork is stealing your week. Automate the right workflows and save 5+ hours per employee—every week. Start with the best candidates and…
Windows Search is turning into a command bar for normal people
Windows Search is becoming a command bar. Ask Copilot turns “find” into “do”—and makes it an IT rollout decision, not a UI tweak…
That Full-Screen “Virus Alert” Is a Scam: How Microsoft Edge Helps Stop Scareware
That full-screen “virus alert” isn’t your PC—it’s a webpage fishing for remote access. Here’s how Edge can shut it down before your team…
Data Services for Business Intelligence
Turn your company’s raw data into on-demand intelligence. Reintivity integrates sources, secures pipelines & builds dashboards to surface real-time insights. Learn more…
Your Firewall, Explained: What It Does, What It Misses, What to Check
Most leaders think “we have a firewall, so we’re fine.” But a firewall isn’t a babysitter—it’s a boundary. Here’s what it misses, and what to check…
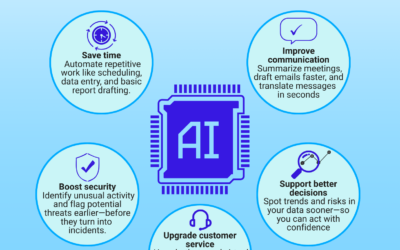
Think AI is only for writing and images?
AI isn’t just for writing and images. It can automate busywork, sharpen decisions, improve service, and flag security risks sooner. See practical uses…
Is your team actually using AI well? Copilot can show you
Copilot licenses don’t guarantee real adoption. New Benchmarks in Viva Insights reveals who’s using it, where, and how often—so you can coach, not police…
Chicago Nonprofit Cyber Hygiene: Break Bad IT Habits & Reduce Wi-Fi Risk Without Breaking Your Budget
Chicago nonprofits: “free” Wi-Fi and small IT shortcuts can trigger big disruption. Break the bad habits, lock down the basics, and protect your mission…
Stop Guessing: Measure Copilot Adoption with the New Benchmarks Dashboard
Rolled out Copilot but unsure who’s using it? Viva Insights’ new Benchmarks dashboard shows usage trends and gaps—so you can improve adoption…
AI Tools Aren’t Enough: How to Build Confidence Across Your Team
Most employees use AI daily—but few are trained. That gap creates hesitation and mistakes. Here’s how to build real AI confidence with support and guardrails…
How to make your team AI-confident
Most employees use AI at work—but many stay quiet, fearing judgment. Build confidence with culture, training, and clear rules so AI becomes a partner…
Chicago Remote-Ready Insurance Hiring: A Secure Tech Stack Guide
Hiring remote insurance talent in Chicago? Your tech stack can speed onboarding—or create risk. Build the Remote-Ready 7 before you scale…
Spam Isn’t Just Annoying Anymore: The Inbox Threat You Can’t Ignore
Spam now looks like invoices, delivery notices, even coworkers. One click can steal passwords or trigger fraud. Here’s how to stop it before it lands…
Word’s New Default: AutoSave to OneDrive (And What It Means for You)
Word now saves new docs to OneDrive by default—so crashes don’t erase hours of work. Prefer local-only files? Here’s what to check before you agree…
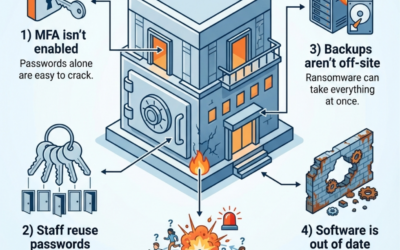
5 Clues your business looks like an easy cyber target
Think you’re too small to be hacked? Missing MFA, reused passwords, no off-site backups, old software, and no breach plan can paint a target. See how to fix…
Never lose a Word document again
Word’s new default AutoSave sends new docs to OneDrive—great for backups, tricky for privacy and control. Love it or hate it, it’s changing how you work…
Copilot is starting to act like a “universal remote” for Microsoft and Google
Copilot is becoming a universal remote for Gmail + Outlook. Fewer tabs, fewer double-books, faster docs and decks. The big question is trust…
One assistant for Outlook, Gmail, and Calendar
Copilot now connects Outlook, Gmail, and Google Calendar in Windows—so you can get answers fast without switching tabs. Here’s what it can do for you…
Build Smarter with Power Platform
Build apps, automate workflows & surface insights fast with Microsoft Power Platform—Reintivity’s low-code experts turn ideas into scalable solutions. Get started…
Spam isn’t “just spam” anymore Cybersecurity Guide
Spam isn’t noise anymore—it’s a delivery system for phishing, malware, and fraud. Learn the simple layers that block most attacks before they reach your inbox…
The Skeptical Leader’s IT Partner Playbook
Your IT shouldn’t feel like a mystery or a constant fire drill. Here’s how to spot real partnership, reduce risk, and build a roadmap that actually works…
Are You Getting Real IT Partnership—or Just Tech Support
Tech is how your organization runs now—not just what it runs on. Learn how to spot real IT partnership, reduce risk, and build a roadmap that scales…
Preview: AI audio translation in Microsoft Edge
Microsoft Edge is testing AI that translates video audio in real time, turning foreign-language training and updates into instant insights. See how it could…
AI live audio translation is coming to Microsoft Edge
AI-powered audio translation in Microsoft Edge could turn global videos into instant training and insights for your team. See how it works (and its limits)…
“I’d Never Fall for That.” Famous Last Words in Healthcare Email Security
Think your team would never click a bad link? In busy clinics, one rushed email can expose patient data and halt care. See how to turn staff into…
Now live: You’re in charge of what Copilot remembers
You choose what Microsoft Copilot remembers, what it forgets, and how personally it supports your work. Take control of your AI assistant and discover how it can…
New in Copilot: You’re in charge of what it remembers
Copilot just got a memory upgrade—so your AI can remember clients, formats, and preferences while you stay in control. See how it works for your team…
From Tech Frustration to Workflow Flow
Clunky tech turns simple work into a slog. The right systems boost security, connection, and morale. Often, all it takes is a few smart changes…