Resources & Content
Featured business & technology resources for growing businesses.
eGuides
In-depth resources to navigate IT solutions
➤
How to
Short videos to get the most out of Microsoft
➤
Product Brochures
Learn about our solutions and offerings
➤
IT Pricing Calculator
Get an estimate for managed IT services
➤
Downtime Calculator
Estimate the cost of an outage event
➤
IT Services Buyer's Guide
Key considerations before purchasing IT services
➤
Password Strength Check
Test your password strength instantly
➤
Cyber Attack Awareness
Watch a hacker in action, stay protected
➤
Have I been Pwned
Check if your email or mobile was hacked
➤
Cyber Risk Score
Measure cybersecurity risk in minutes—fast, private, actionable
➤
Books
2 books to secure enhance and catapult your business into tomorrow
➤
ROI Calculator
Estimate the return on your technology investment in minutes
➤

PowerPoint “Reuse Slides” Is Gone: Here’s the Workaround
If “Reuse Slides” vanished in PowerPoint, you’re not imagining it. Here are two quick ways to reuse slides and keep formatting mostly intact…

Human Firewall: The People-First Playbook for Blocking Phishing and Breaches
Most breaches start with a click—not a “hack.” Your best defense is trained people who spot the red flags and report fast. Here’s how to build that…

PowerPoint Removed “Reuse Slides” — Here’s the Fastest Clean Replacement Workflow
PowerPoint retired “Reuse Slides,” making deck reuse harder. Here’s the fastest drag-and-drop workflow to keep branding clean and save hours…

When Your Tools Fight Back: The Friction Audit That Sets Up a Better Cloud Move
Most IT pain isn’t outages—it’s daily friction. Audit the drag, fix quick wins, then decide if cloud truly simplifies your next chapter…
Password resets are a tax. Passkeys are how we stop paying it.
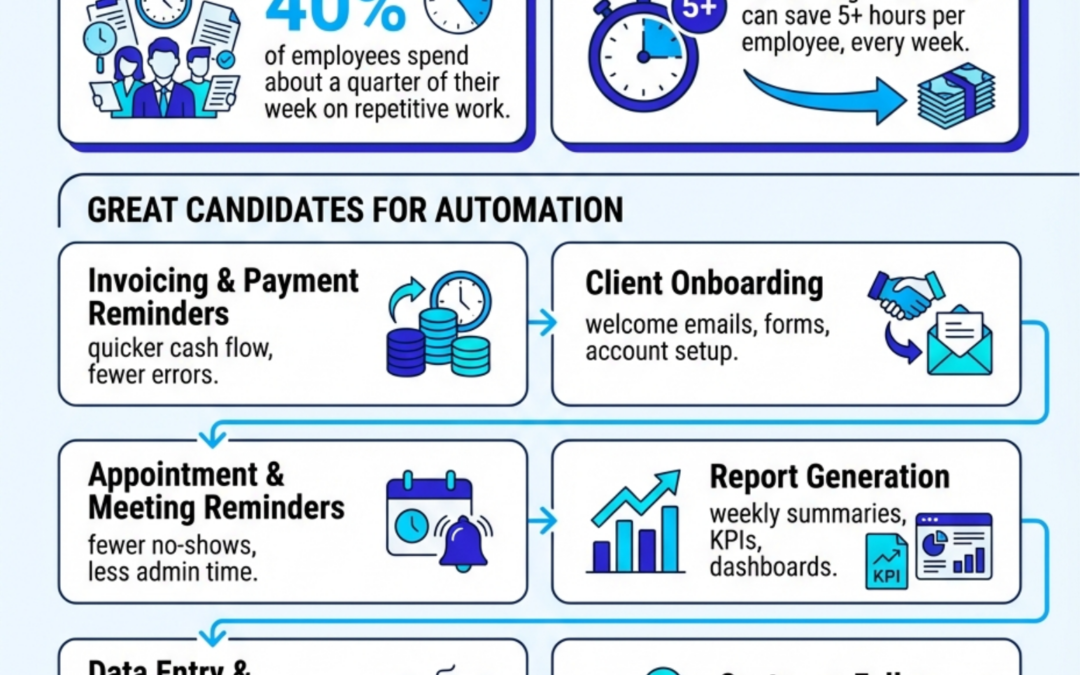
Busywork to Breakthrough: What to Automate First
Busywork is stealing your week. Automate the right workflows and save 5+ hours per employee—every week. Start with the best candidates and…

Windows Search is turning into a command bar for normal people
Windows Search is becoming a command bar. Ask Copilot turns “find” into “do”—and makes it an IT rollout decision, not a UI tweak…

That Full-Screen “Virus Alert” Is a Scam: How Microsoft Edge Helps Stop Scareware
That full-screen “virus alert” isn’t your PC—it’s a webpage fishing for remote access. Here’s how Edge can shut it down before your team…
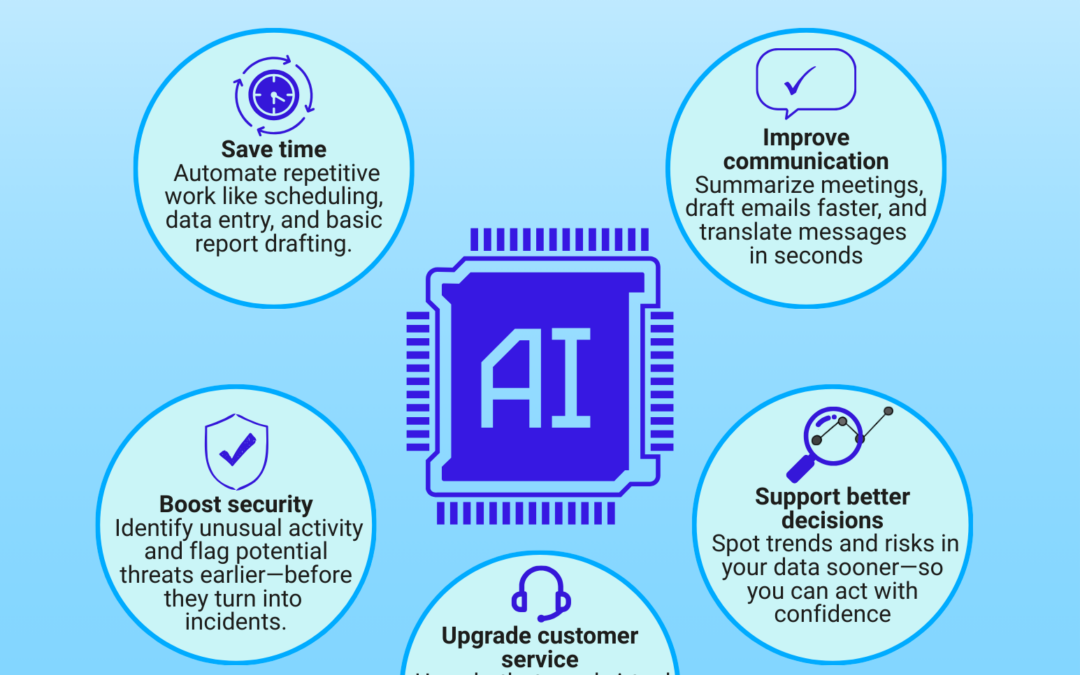
Think AI is only for writing and images?
AI isn’t just for writing and images. It can automate busywork, sharpen decisions, improve service, and flag security risks sooner. See practical uses…

Data Services for Business Intelligence
Turn your company’s raw data into on-demand intelligence. Reintivity integrates sources, secures pipelines & builds dashboards to surface real-time insights. Learn more…
With rapidly evolving technology, our experts know how to leverage modern innovations to solve your unique business challenges.

Stable Systems, Steady Care: How a Dialysis Center Turned a Server Crisis into a Strategic Win
A server crash nearly derailed a busy dialysis center. See how a same-day rescue turned into predictable systems and steadier patient care…
Solving industry software technology challenges today
Is your team actually using AI well? Copilot can show you
Copilot licenses don’t guarantee real adoption. New Benchmarks in Viva Insights reveals who’s using it, where, and how often—so you can coach, not police…

Chicago Nonprofit Cyber Hygiene: Break Bad IT Habits & Reduce Wi-Fi Risk Without Breaking Your Budget
Chicago nonprofits: “free” Wi-Fi and small IT shortcuts can trigger big disruption. Break the bad habits, lock down the basics, and protect your mission…

How to make your team AI-confident
Most employees use AI at work—but many stay quiet, fearing judgment. Build confidence with culture, training, and clear rules so AI becomes a partner…

Chicago Remote-Ready Insurance Hiring: A Secure Tech Stack Guide
Hiring remote insurance talent in Chicago? Your tech stack can speed onboarding—or create risk. Build the Remote-Ready 7 before you scale…
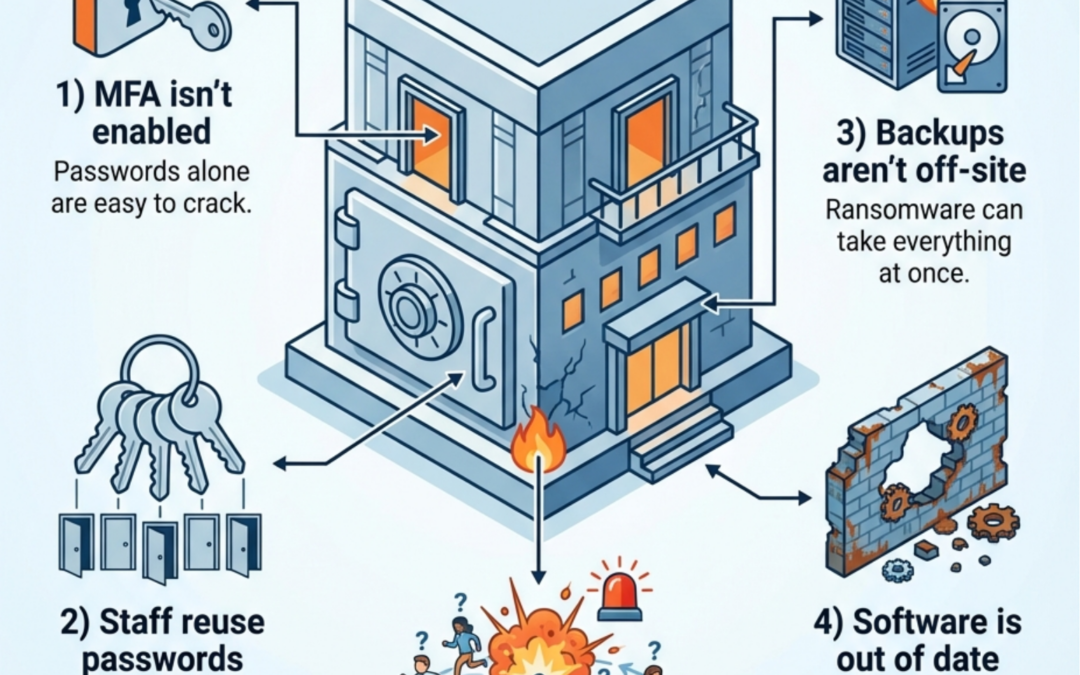
5 Clues your business looks like an easy cyber target

Never lose a Word document again
Word’s new default AutoSave sends new docs to OneDrive—great for backups, tricky for privacy and control. Love it or hate it, it’s changing how you work…

Copilot is starting to act like a “universal remote” for Microsoft and Google
Copilot is becoming a universal remote for Gmail + Outlook. Fewer tabs, fewer double-books, faster docs and decks. The big question is trust…

AI live audio translation is coming to Microsoft Edge
AI-powered audio translation in Microsoft Edge could turn global videos into instant training and insights for your team. See how it works (and its limits)…

Tech mistakes Chicagoland nonprofits can’t afford to ignore
If your nonprofit is running on workarounds, it is time to fix the fundamentals before the next outage, breach, or board question turns into…

