AI browsers can save time, but may send what you view to the cloud. Before you approve them at work, set guardrails and train users to…
Operations & Support
Consider this before using AI-enabled browsers at work
AI-enabled browsers can summarize and automate work, but they may also send sensitive on-screen data to the cloud. Before you roll them out, make sure…
Tech mistakes Chicagoland nonprofits can’t afford to ignore
If your nonprofit is running on workarounds, it is time to fix the fundamentals before the next outage, breach, or board question turns into…
Human Firewall: The People-First Playbook for Blocking Phishing and Breaches
Most breaches start with a click—not a “hack.” Your best defense is trained people who spot the red flags and report fast. Here’s how to build that…
PowerPoint “Reuse Slides” Is Gone: Here’s the Workaround
If “Reuse Slides” vanished in PowerPoint, you’re not imagining it. Here are two quick ways to reuse slides and keep formatting mostly intact…
PowerPoint Removed “Reuse Slides” — Here’s the Fastest Clean Replacement Workflow
PowerPoint retired “Reuse Slides,” making deck reuse harder. Here’s the fastest drag-and-drop workflow to keep branding clean and save hours…
Edge Passkeys Now Sync Across Devices
Password resets burn time. Edge can now sync passkeys across devices, so your team signs in with face, fingerprint, or PIN and skips the reset loop…
When Your Tools Fight Back: The Friction Audit That Sets Up a Better Cloud Move
Most IT pain isn’t outages—it’s daily friction. Audit the drag, fix quick wins, then decide if cloud truly simplifies your next chapter…
Password resets are a tax. Passkeys are how we stop paying it.
Password resets are a tax. Passkeys can cut the bill—but only if they’re practical. Edge passkey sync removes a key objection, with a catch…
Ask Copilot: The Windows 11 Shortcut You Can Turn Off
Ask Copilot may land on your Windows 11 taskbar. Type what you need, and settings happen fast. It’s optional, and it could save your team…
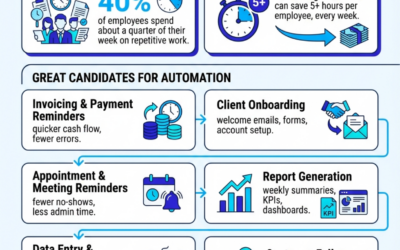
Busywork to Breakthrough: What to Automate First
Busywork is stealing your week. Automate the right workflows and save 5+ hours per employee—every week. Start with the best candidates and…
Windows Search is turning into a command bar for normal people
Windows Search is becoming a command bar. Ask Copilot turns “find” into “do”—and makes it an IT rollout decision, not a UI tweak…
Microsoft Edge just rolled out a new scam protection feature
Those “your computer is infected” pop-ups are evolving fast. Edge now blocks many of them automatically with AI, but only if you…
Firewall + Web Filtering: Stop Threats Before They Land
Your firewall checks traffic. Web filtering helps prevent risky clicks, fake login pages, and malware traps. Not sure yours matches today’s threats…
That Full-Screen “Virus Alert” Is a Scam: How Microsoft Edge Helps Stop Scareware
That full-screen “virus alert” isn’t your PC—it’s a webpage fishing for remote access. Here’s how Edge can shut it down before your team…
Your Firewall, Explained: What It Does, What It Misses, What to Check
Most leaders think “we have a firewall, so we’re fine.” But a firewall isn’t a babysitter—it’s a boundary. Here’s what it misses, and what to check…
Chicago Nonprofit Cyber Hygiene: Break Bad IT Habits & Reduce Wi-Fi Risk Without Breaking Your Budget
Chicago nonprofits: “free” Wi-Fi and small IT shortcuts can trigger big disruption. Break the bad habits, lock down the basics, and protect your mission…
Chicago Remote-Ready Insurance Hiring: A Secure Tech Stack Guide
Hiring remote insurance talent in Chicago? Your tech stack can speed onboarding—or create risk. Build the Remote-Ready 7 before you scale…
Spam Isn’t Just Annoying Anymore: The Inbox Threat You Can’t Ignore
Spam now looks like invoices, delivery notices, even coworkers. One click can steal passwords or trigger fraud. Here’s how to stop it before it lands…
Word’s New Default: AutoSave to OneDrive (And What It Means for You)
Word now saves new docs to OneDrive by default—so crashes don’t erase hours of work. Prefer local-only files? Here’s what to check before you agree…
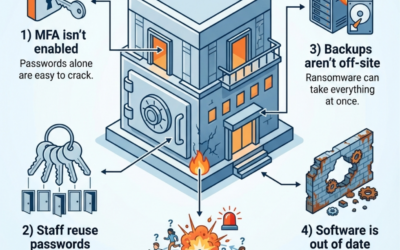
5 Clues your business looks like an easy cyber target
Think you’re too small to be hacked? Missing MFA, reused passwords, no off-site backups, old software, and no breach plan can paint a target. See how to fix…
Spam isn’t “just spam” anymore Cybersecurity Guide
Spam isn’t noise anymore—it’s a delivery system for phishing, malware, and fraud. Learn the simple layers that block most attacks before they reach your inbox…
The Skeptical Leader’s IT Partner Playbook
Your IT shouldn’t feel like a mystery or a constant fire drill. Here’s how to spot real partnership, reduce risk, and build a roadmap that actually works…
Are You Getting Real IT Partnership—or Just Tech Support
Tech is how your organization runs now—not just what it runs on. Learn how to spot real IT partnership, reduce risk, and build a roadmap that scales…
Don’t Be Fooled by Fake Apps: Hidden Malware Threats to Your Business
Cybercriminals hide malware inside fake apps that look real. Even careful staff can be fooled, putting your business at risk. See how to protect…
Watch out for fake apps hiding malware
Fake look-alike apps are tricking staff and slipping malware onto work devices. Learn how to spot the red flags before your data is exposed…
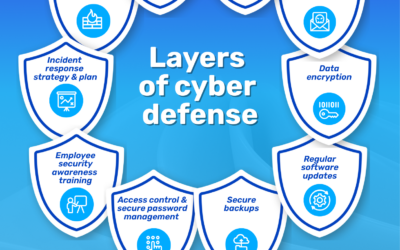
Layered Security: Why One Tool Is Never Enough
Cybersecurity isn’t one magic tool. Real protection comes from stacked layers that catch what others miss. The real question is how many layers you have…
Old School Tech, New School Threats: How “Retired” Devices Put K–12 Data at Risk
Your old school laptops aren’t just clutter. Without proper wiping, they can leak student records and staff data. Discover how a simple device plan can…
AI vs. AI: Inside the Next Wave of Cybercrime
AI is supercharging cyberattacks—and rewriting the rules of defense. Discover how AI-driven malware works and what your business must do next…
Managed Software Technology Services
Reintivity’s Managed Software Technology Services bring proactive maintenance, patching & real-time monitoring—turning IT from reactive cost to strategic asset. Find out how…