Our Blog
Stay up to date with our latest posts.
Is “technical debt” slowing your business growth?
If IT feels slow, fragile, or harder to manage, technical debt may be the reason. With Windows 10 support ended, it’s time to reduce risk by…
What We Do: Consulting, Management & Sourcing
Need help improving your business processes and technology infrastructure to stay competitive in today's fast-paced market? Reintivity offers comprehensive solutions aimed at enhancing business processes and technology infrastructures, leveraging their expertise in...
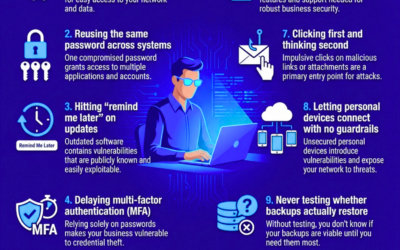
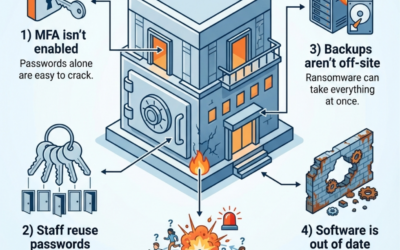
10 Things Attackers Hope Your Business Keeps Doing
Attackers count on small habits, not Hollywood hacks. See the 10 things they hope your business keeps doing and where to tighten up first…
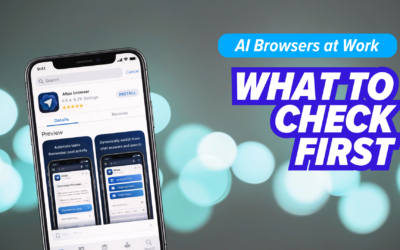
AI Browsers at Work: Convenience vs Risk
AI browsers can save time, but may send what you view to the cloud. Before you approve them at work, set guardrails and train users to…
Consider this before using AI-enabled browsers at work
AI-enabled browsers can summarize and automate work, but they may also send sensitive on-screen data to the cloud. Before you roll them out, make sure…
Tech mistakes Chicagoland nonprofits can’t afford to ignore
If your nonprofit is running on workarounds, it is time to fix the fundamentals before the next outage, breach, or board question turns into…
Human Firewall: The People-First Playbook for Blocking Phishing and Breaches
Most breaches start with a click—not a “hack.” Your best defense is trained people who spot the red flags and report fast. Here’s how to build that…
PowerPoint “Reuse Slides” Is Gone: Here’s the Workaround
If “Reuse Slides” vanished in PowerPoint, you’re not imagining it. Here are two quick ways to reuse slides and keep formatting mostly intact…
PowerPoint Removed “Reuse Slides” — Here’s the Fastest Clean Replacement Workflow
PowerPoint retired “Reuse Slides,” making deck reuse harder. Here’s the fastest drag-and-drop workflow to keep branding clean and save hours…
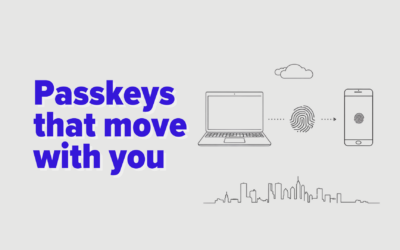
Edge Passkeys Now Sync Across Devices
Password resets burn time. Edge can now sync passkeys across devices, so your team signs in with face, fingerprint, or PIN and skips the reset loop…
When Your Tools Fight Back: The Friction Audit That Sets Up a Better Cloud Move
Most IT pain isn’t outages—it’s daily friction. Audit the drag, fix quick wins, then decide if cloud truly simplifies your next chapter…
Password resets are a tax. Passkeys are how we stop paying it.
Password resets are a tax. Passkeys can cut the bill—but only if they’re practical. Edge passkey sync removes a key objection, with a catch…
Ask Copilot: The Windows 11 Shortcut You Can Turn Off
Ask Copilot may land on your Windows 11 taskbar. Type what you need, and settings happen fast. It’s optional, and it could save your team…
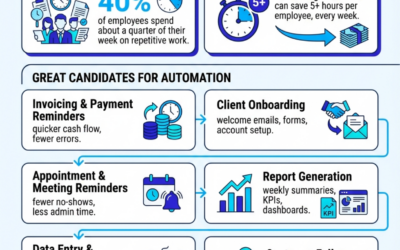
Busywork to Breakthrough: What to Automate First
Busywork is stealing your week. Automate the right workflows and save 5+ hours per employee—every week. Start with the best candidates and…
Windows Search is turning into a command bar for normal people
Windows Search is becoming a command bar. Ask Copilot turns “find” into “do”—and makes it an IT rollout decision, not a UI tweak…
Microsoft Edge just rolled out a new scam protection feature
Those “your computer is infected” pop-ups are evolving fast. Edge now blocks many of them automatically with AI, but only if you…
Firewall + Web Filtering: Stop Threats Before They Land
Your firewall checks traffic. Web filtering helps prevent risky clicks, fake login pages, and malware traps. Not sure yours matches today’s threats…
That Full-Screen “Virus Alert” Is a Scam: How Microsoft Edge Helps Stop Scareware
That full-screen “virus alert” isn’t your PC—it’s a webpage fishing for remote access. Here’s how Edge can shut it down before your team…
Data Services for Business Intelligence
Turn your company’s raw data into on-demand intelligence. Reintivity integrates sources, secures pipelines & builds dashboards to surface real-time insights. Learn more…
Your Firewall, Explained: What It Does, What It Misses, What to Check
Most leaders think “we have a firewall, so we’re fine.” But a firewall isn’t a babysitter—it’s a boundary. Here’s what it misses, and what to check…
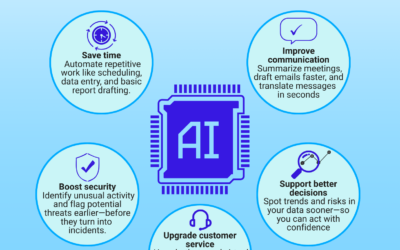
Think AI is only for writing and images?
AI isn’t just for writing and images. It can automate busywork, sharpen decisions, improve service, and flag security risks sooner. See practical uses…
Is your team actually using AI well? Copilot can show you
Copilot licenses don’t guarantee real adoption. New Benchmarks in Viva Insights reveals who’s using it, where, and how often—so you can coach, not police…
Chicago Nonprofit Cyber Hygiene: Break Bad IT Habits & Reduce Wi-Fi Risk Without Breaking Your Budget
Chicago nonprofits: “free” Wi-Fi and small IT shortcuts can trigger big disruption. Break the bad habits, lock down the basics, and protect your mission…
Stop Guessing: Measure Copilot Adoption with the New Benchmarks Dashboard
Rolled out Copilot but unsure who’s using it? Viva Insights’ new Benchmarks dashboard shows usage trends and gaps—so you can improve adoption…
AI Tools Aren’t Enough: How to Build Confidence Across Your Team
Most employees use AI daily—but few are trained. That gap creates hesitation and mistakes. Here’s how to build real AI confidence with support and guardrails…
How to make your team AI-confident
Most employees use AI at work—but many stay quiet, fearing judgment. Build confidence with culture, training, and clear rules so AI becomes a partner…
Chicago Remote-Ready Insurance Hiring: A Secure Tech Stack Guide
Hiring remote insurance talent in Chicago? Your tech stack can speed onboarding—or create risk. Build the Remote-Ready 7 before you scale…
Spam Isn’t Just Annoying Anymore: The Inbox Threat You Can’t Ignore
Spam now looks like invoices, delivery notices, even coworkers. One click can steal passwords or trigger fraud. Here’s how to stop it before it lands…
Word’s New Default: AutoSave to OneDrive (And What It Means for You)
Word now saves new docs to OneDrive by default—so crashes don’t erase hours of work. Prefer local-only files? Here’s what to check before you agree…
5 Clues your business looks like an easy cyber target
Think you’re too small to be hacked? Missing MFA, reused passwords, no off-site backups, old software, and no breach plan can paint a target. See how to fix…