Resources & Content
Featured business & technology resources for growing businesses.
eGuides
In-depth resources to navigate IT solutions
➤
How to
Short videos to get the most out of Microsoft
➤
Product Brochures
Learn about our solutions and offerings
➤
IT Pricing Calculator
Get an estimate for managed IT services
➤
Downtime Calculator
Estimate the cost of an outage event
➤
IT Services Buyer's Guide
Key considerations before purchasing IT services
➤
Password Strength Check
Test your password strength instantly
➤
Cyber Attack Awareness
Watch a hacker in action, stay protected
➤
Have I been Pwned
Check if your email or mobile was hacked
➤
Cyber Risk Score
Measure cybersecurity risk in minutes—fast, private, actionable
➤
Books
2 books to secure enhance and catapult your business into tomorrow
➤
ROI Calculator
Estimate the return on your technology investment in minutes
➤

Stop Guessing: Measure Copilot Adoption with the New Benchmarks Dashboard
Rolled out Copilot but unsure who’s using it? Viva Insights’ new Benchmarks dashboard shows usage trends and gaps—so you can improve adoption…
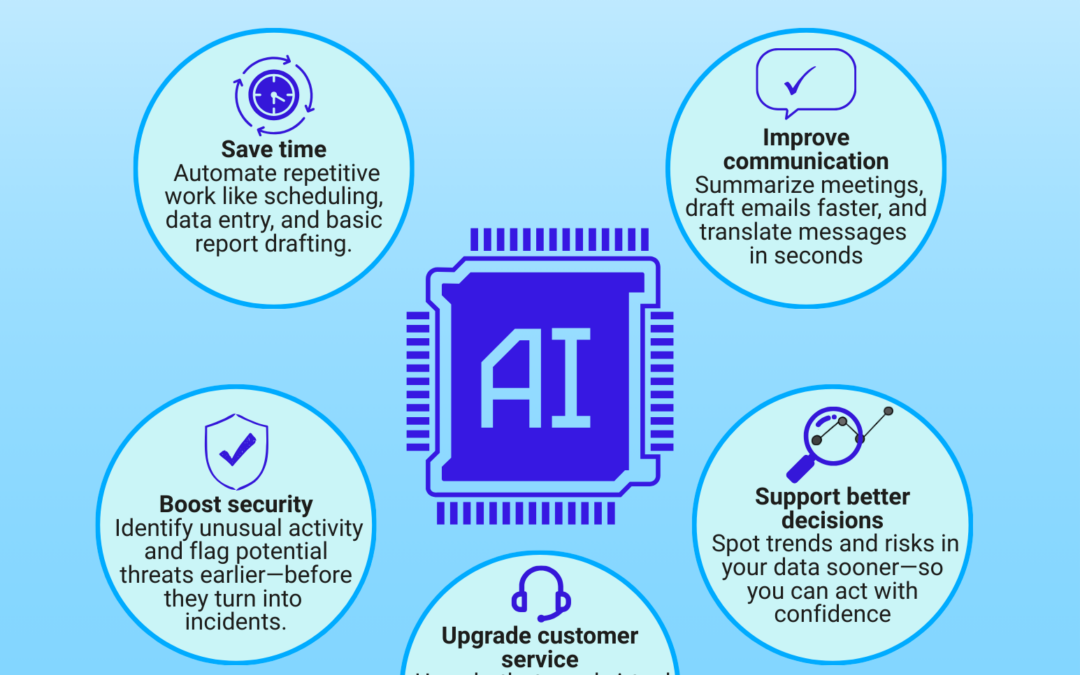
Think AI is only for writing and images?
AI isn’t just for writing and images. It can automate busywork, sharpen decisions, improve service, and flag security risks sooner. See practical uses…
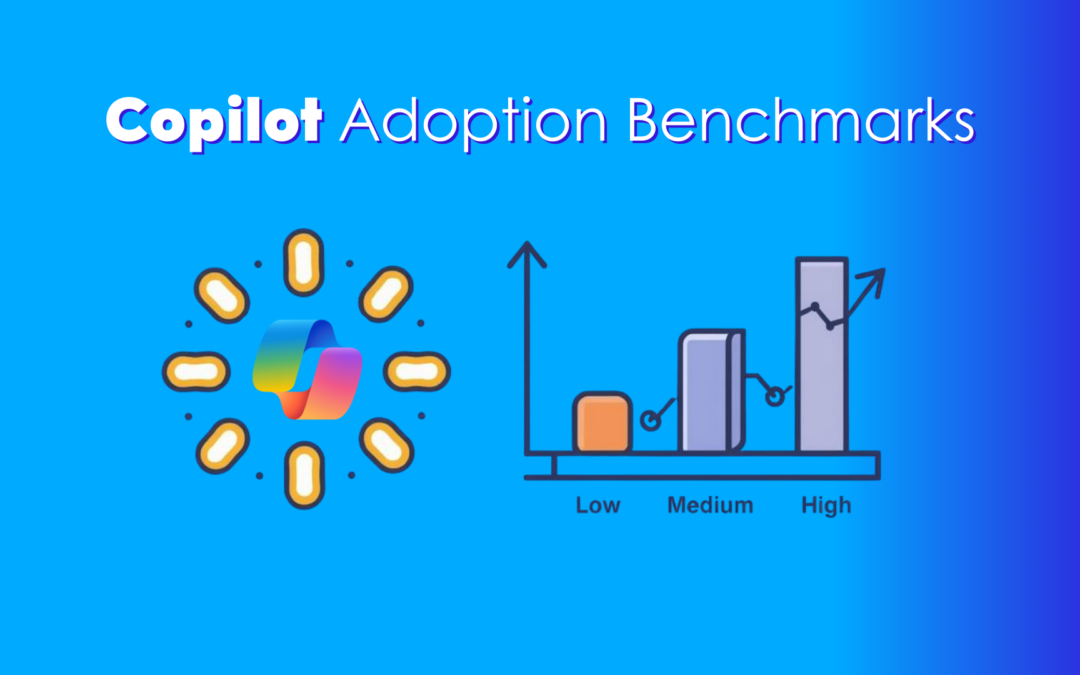
Is your team actually using AI well? Copilot can show you
Copilot licenses don’t guarantee real adoption. New Benchmarks in Viva Insights reveals who’s using it, where, and how often—so you can coach, not police…

Chicago Nonprofit Cyber Hygiene: Break Bad IT Habits & Reduce Wi-Fi Risk Without Breaking Your Budget
Chicago nonprofits: “free” Wi-Fi and small IT shortcuts can trigger big disruption. Break the bad habits, lock down the basics, and protect your mission…

How to make your team AI-confident
Most employees use AI at work—but many stay quiet, fearing judgment. Build confidence with culture, training, and clear rules so AI becomes a partner…

Chicago Remote-Ready Insurance Hiring: A Secure Tech Stack Guide
Hiring remote insurance talent in Chicago? Your tech stack can speed onboarding—or create risk. Build the Remote-Ready 7 before you scale…
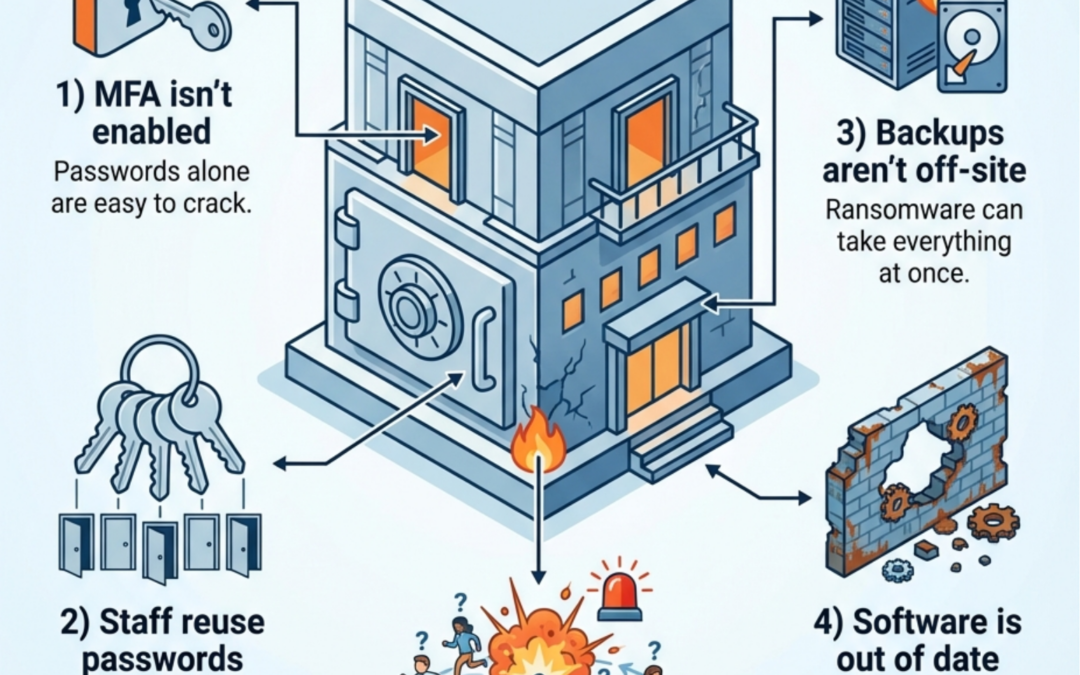
5 Clues your business looks like an easy cyber target

Never lose a Word document again
Word’s new default AutoSave sends new docs to OneDrive—great for backups, tricky for privacy and control. Love it or hate it, it’s changing how you work…

Copilot is starting to act like a “universal remote” for Microsoft and Google
Copilot is becoming a universal remote for Gmail + Outlook. Fewer tabs, fewer double-books, faster docs and decks. The big question is trust…

Build Smarter with Power Platform
Build apps, automate workflows & surface insights fast with Microsoft Power Platform—Reintivity’s low-code experts turn ideas into scalable solutions. Get started…
With rapidly evolving technology, our experts know how to leverage modern innovations to solve your unique business challenges.

Stable Systems, Steady Care: How a Dialysis Center Turned a Server Crisis into a Strategic Win
A server crash nearly derailed a busy dialysis center. See how a same-day rescue turned into predictable systems and steadier patient care…
Solving industry software technology challenges today

AI live audio translation is coming to Microsoft Edge
AI-powered audio translation in Microsoft Edge could turn global videos into instant training and insights for your team. See how it works (and its limits)…

“I’d Never Fall for That.” Famous Last Words in Healthcare Email Security
Think your team would never click a bad link? In busy clinics, one rushed email can expose patient data and halt care. See how to turn staff into…
New in Copilot: You’re in charge of what it remembers
Copilot just got a memory upgrade—so your AI can remember clients, formats, and preferences while you stay in control. See how it works for your team…

From Tech Frustration to Workflow Flow
Clunky tech turns simple work into a slog. The right systems boost security, connection, and morale. Often, all it takes is a few smart changes…

Watch out for fake apps hiding malware
Fake look-alike apps are tricking staff and slipping malware onto work devices. Learn how to spot the red flags before your data is exposed…
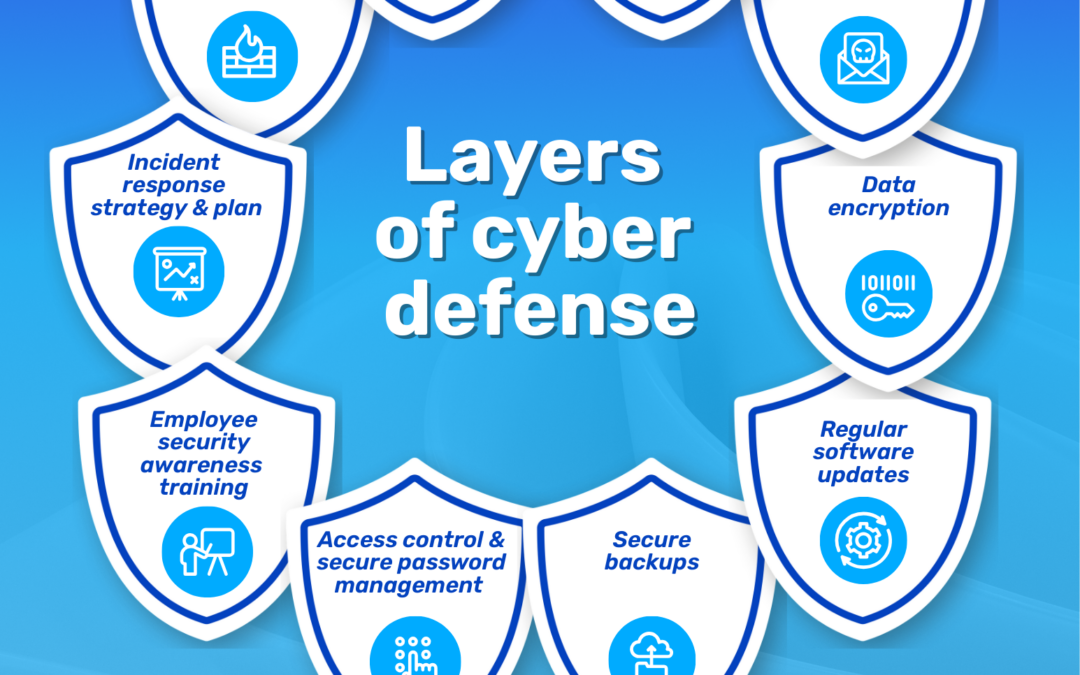
Layered Security: Why One Tool Is Never Enough
Cybersecurity isn’t one magic tool. Real protection comes from stacked layers that catch what others miss. The real question is how many layers you have…

Old School Tech, New School Threats: How “Retired” Devices Put K–12 Data at Risk
Your old school laptops aren’t just clutter. Without proper wiping, they can leak student records and staff data. Discover how a simple device plan can…

When 4 Out of 5 Cyberattacks Are Run by AI
4 out of 5 cyberattacks now use AI, hitting SMBs at machine speed. See how to fight back with layered defenses before attackers get smarter…


